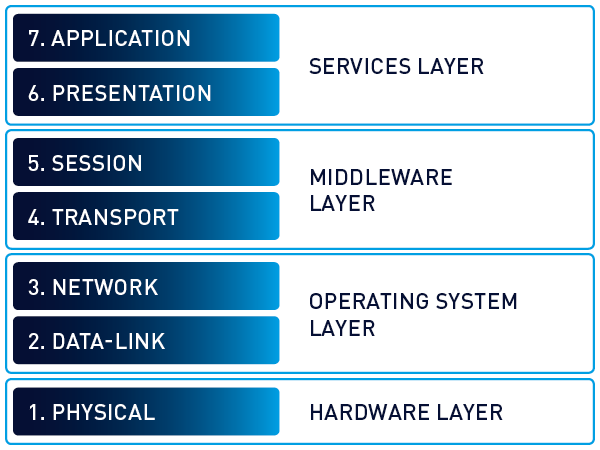
Layer 8 Hacking - Linking the OSI Model with the NIST Triangle
4.6 (741) · $ 14.00 · In stock

Layer 8 Hacking can be defined as hacking above and beyond the technical layers; hacking by targeting the user, the business processes, or the organization i
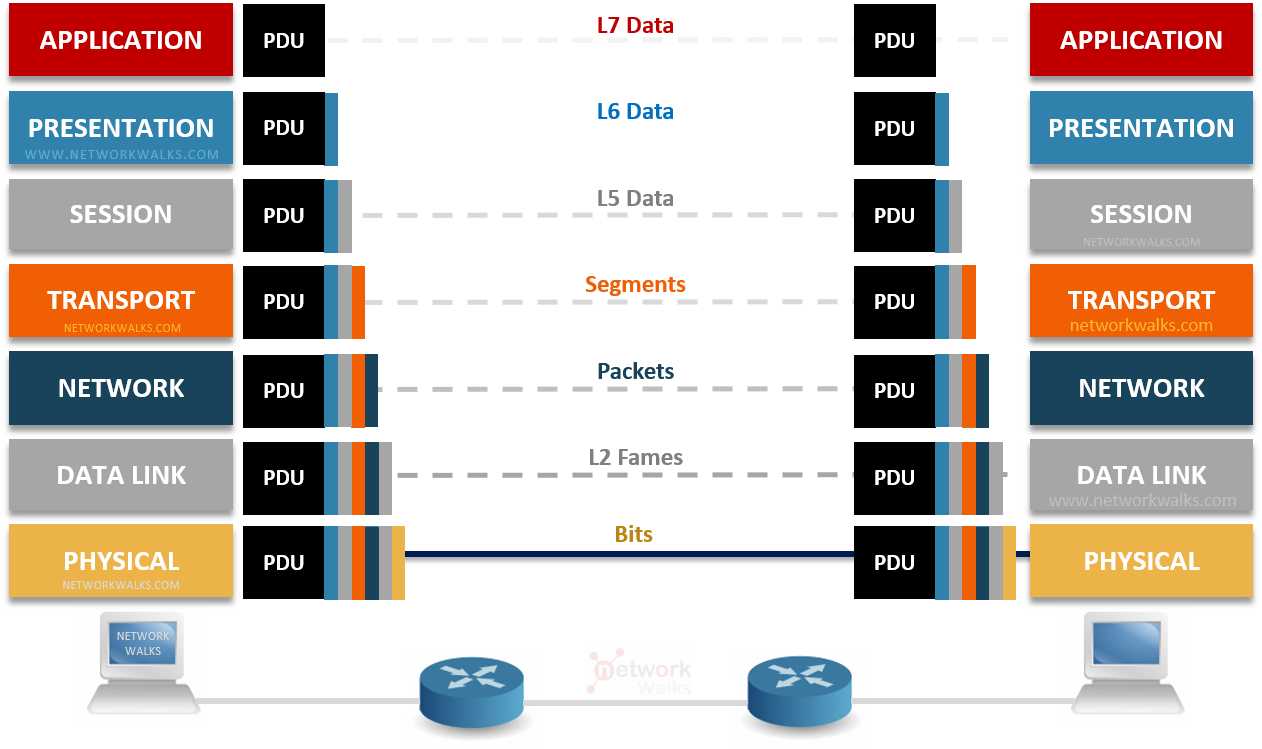
OSI Model (Open Systems Interconnection Model)

8th Layer in OSI Model…. Twitter recently disclosed that its own
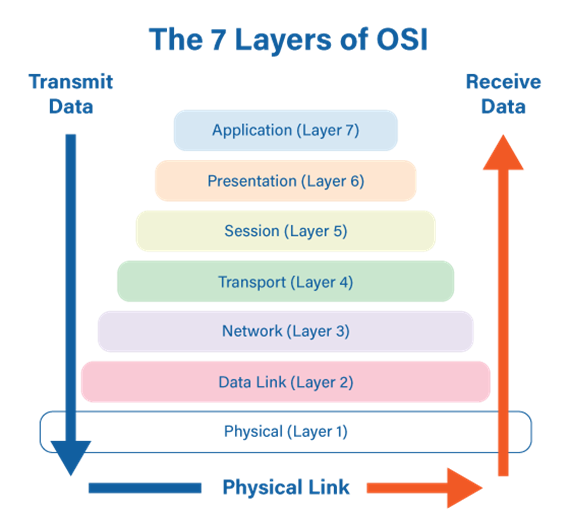
An overview of the OSI model and its security threats
How VMware can Secure Mobile Endpoints with Threat Defense (MTD
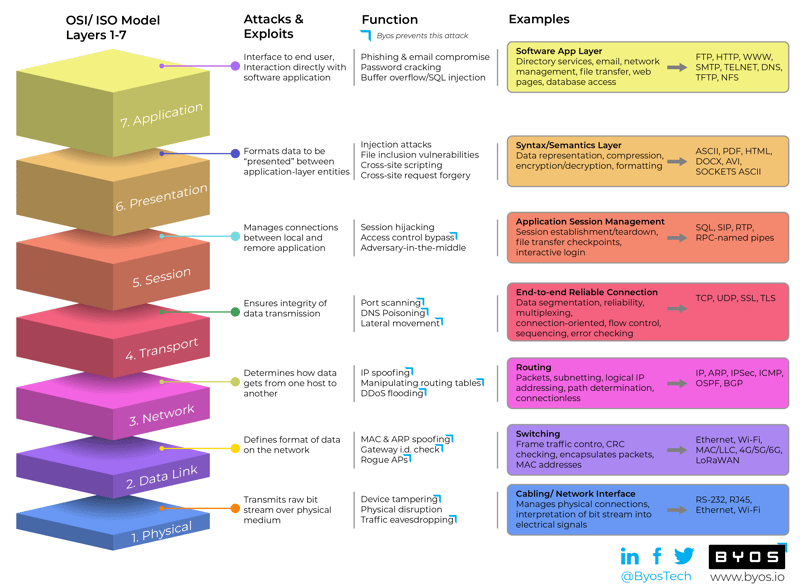
How Cyber Adversaries Attack Each of the OSI Layers 1-7

The elements of IACS security programme development according to

Seven Layers of OSI Model in an easy way
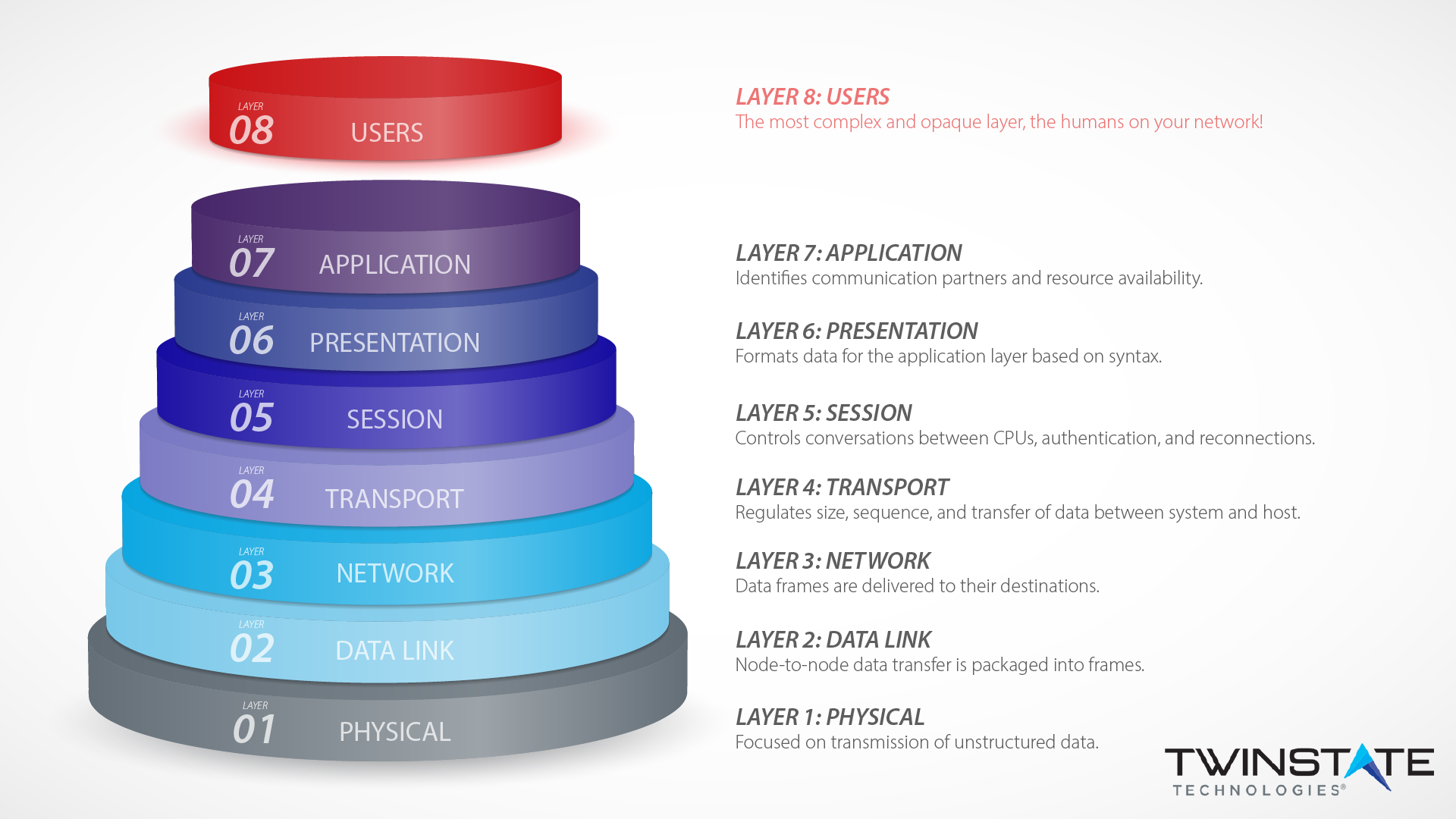
Layer 8 Technology: How We Protect Users at our Plattsburgh Office
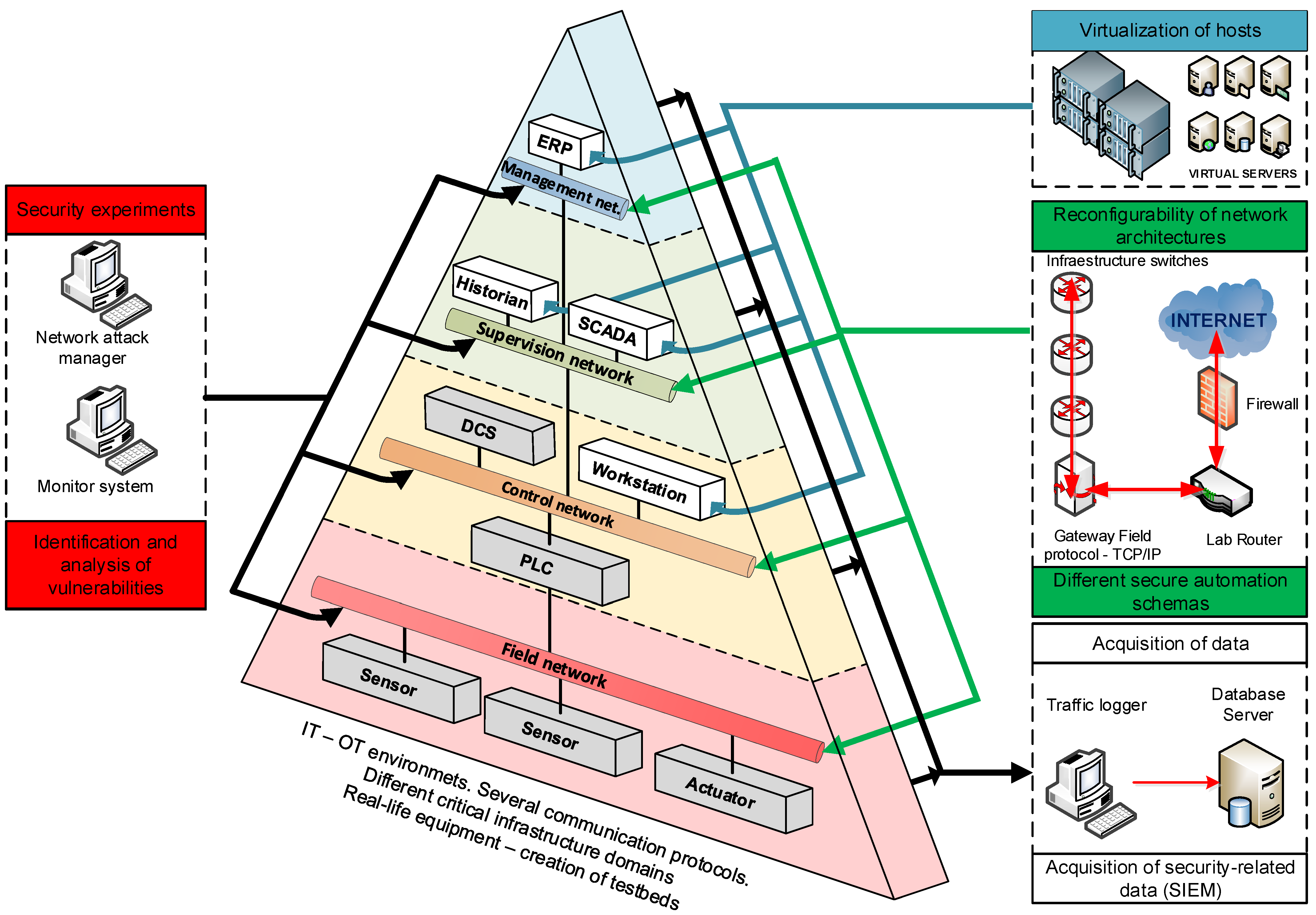
Applied Sciences, Free Full-Text

Ethical hacking for IoT: Security issues, challenges, solutions
Glossaries learnonline