Tighten SSH access to your cloud resources using short-lived SSH certificates
5 (339) · $ 12.50 · In stock

SSH access using public private key based authentication has several drawbacks that could potentially compromise your organization’s SSH access security. SSH certificate based authentication is a great alternative that addresses most of these security problems.

TSCC User Guide
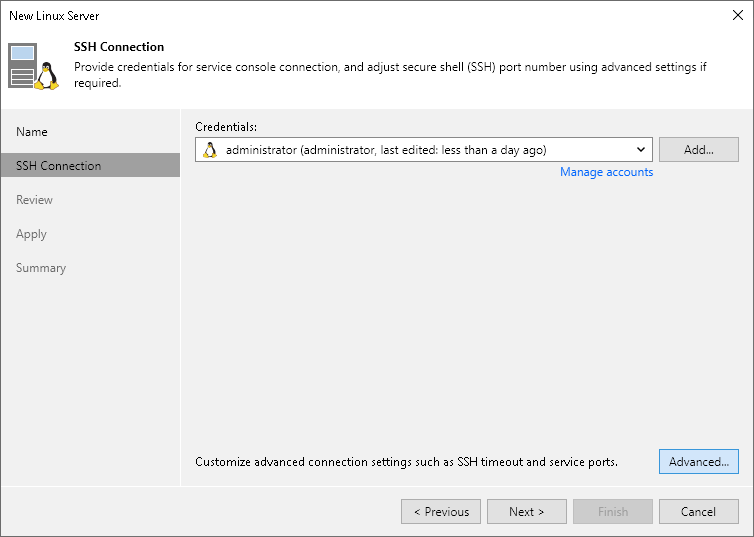
Step 3. Specify Credentials and SSH Settings - User Guide for

SSH Communications Security Introduces Access Management at the

SSH Key Management Overview & 10 Best Practices
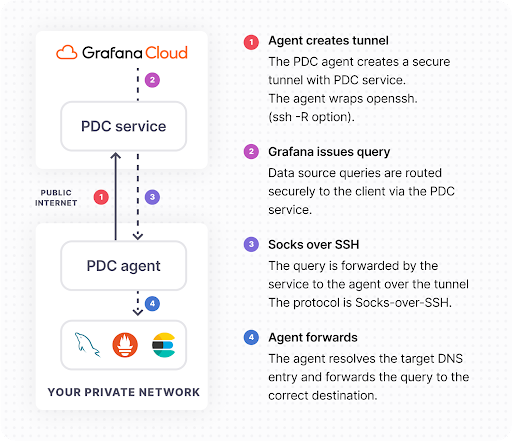
Private data source connect (PDC)
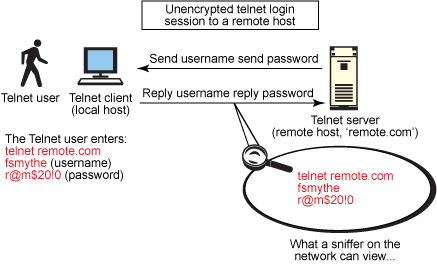
Getting started with SSH security and configuration - IBM Developer
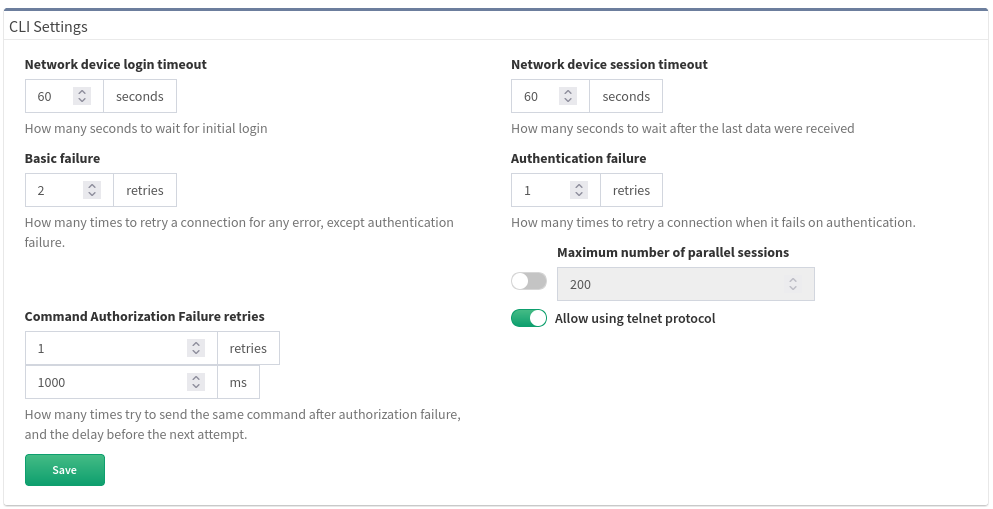
SSH/TELNET - IP Fabric Documentation Portal
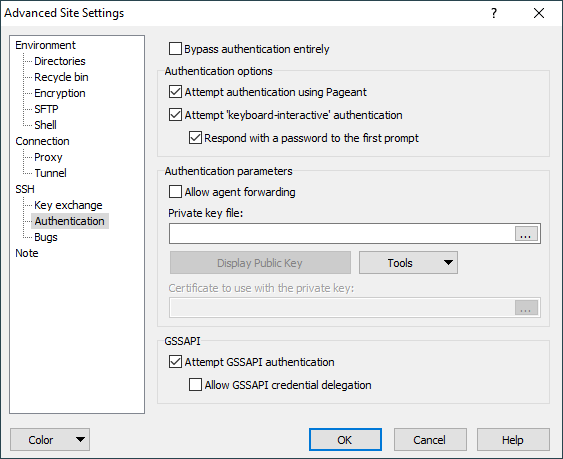
The Authentication Page (Advanced Site Settings dialog) :: WinSCP
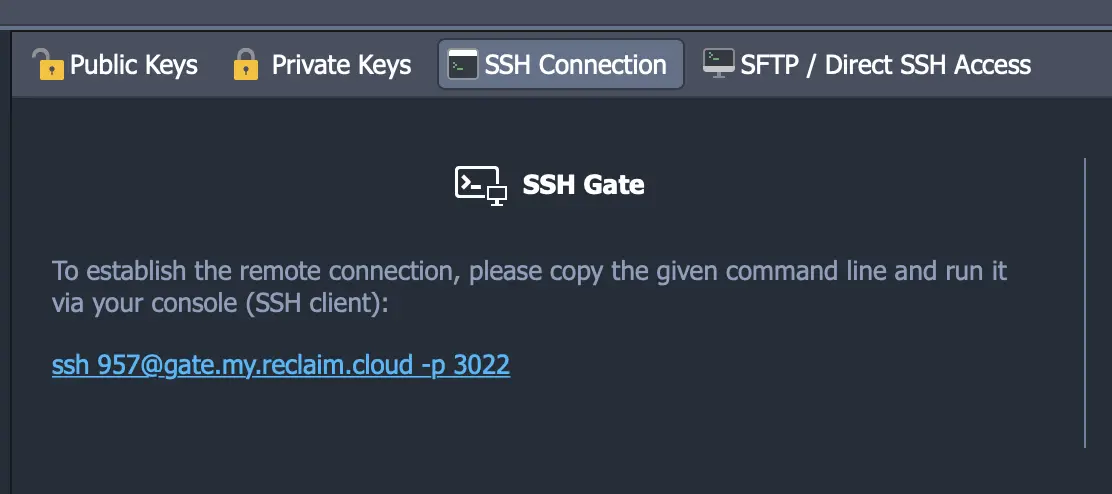
A Tip for Quick SSH Access on Reclaim Cloud







