Attackers can force Echos to hack themselves with self
5 (72) · $ 27.50 · In stock

Popular “smart” device follows commands issued by its own speaker. What could go wrong?

Echo security loophole exploited to make them hack

Pew! Pew! Researcher Uses Laser to Steal Data From a Tiny Chip

Google Home and Echo apps just exposed a very dangerous security

Man-the-Middle (MiTM) Attack with ARPspoofing
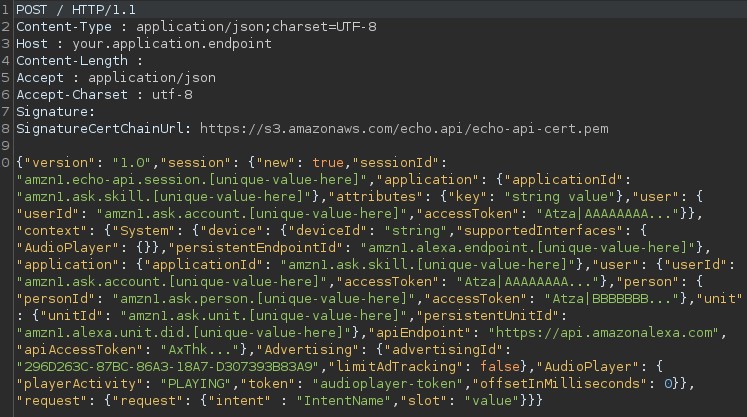
Mapping vulnerabilities in echo using alexa skills

Certified Ethical Hacker quick test prep cheat sheet

Internet of things' security introduction for EMS leaders
How Hackers Outwit All Efforts to Stop Them: It's a Cyber Pandemic.

The Mirai Confessions: Three Young Hackers Who Built a Web-Killing

Hacking reality
You may also like







