Comparison of Data Hash generated using Hu moments on KNIX vs distorted
4.9 (541) · $ 18.00 · In stock


A new design paradigm for provably secure keyless hash function
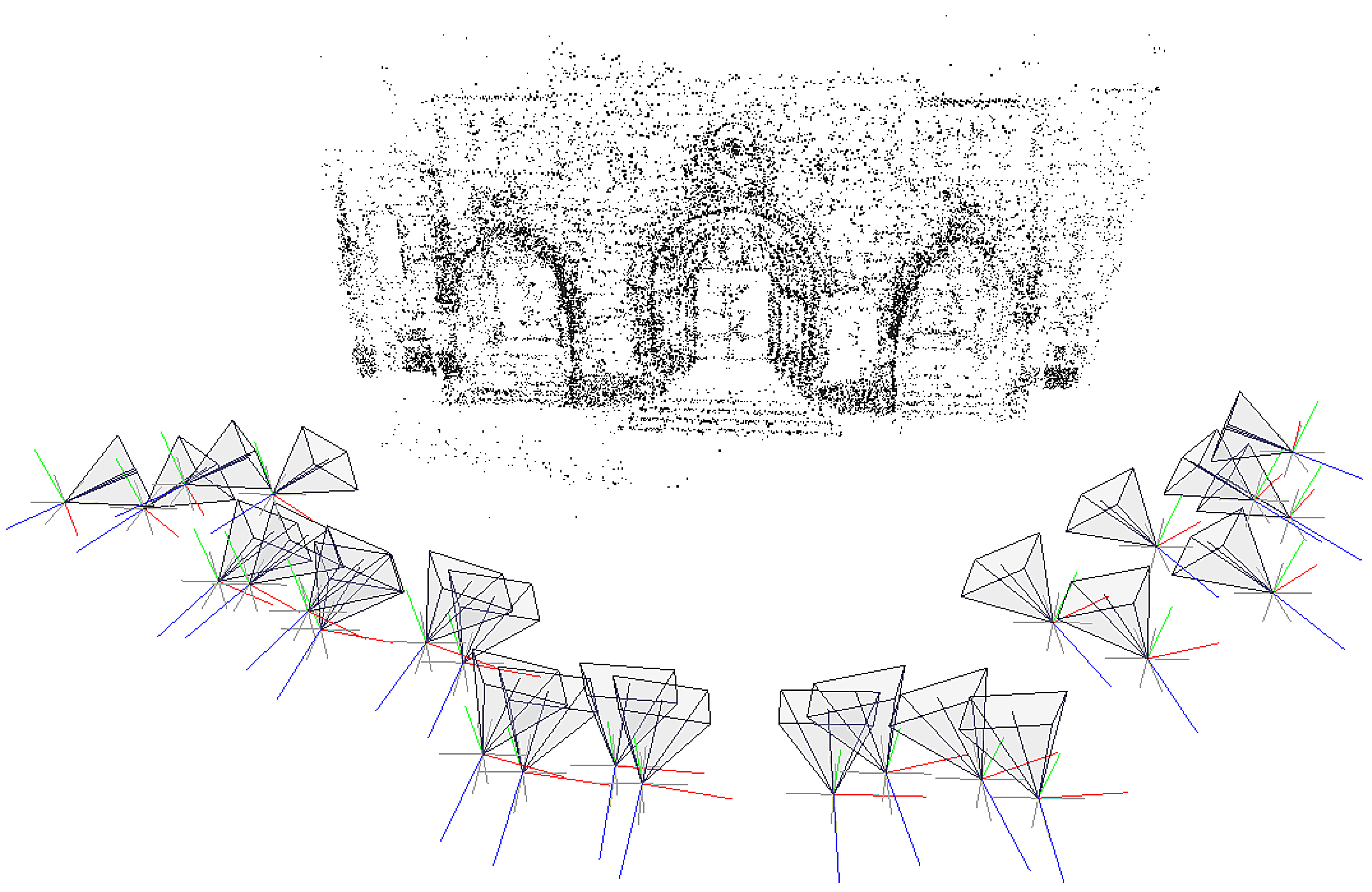
Applied Sciences, Free Full-Text

A. Shenbagavalli's research works Tamilnadu College of Engineering, Coimbatore (TCE) and other places
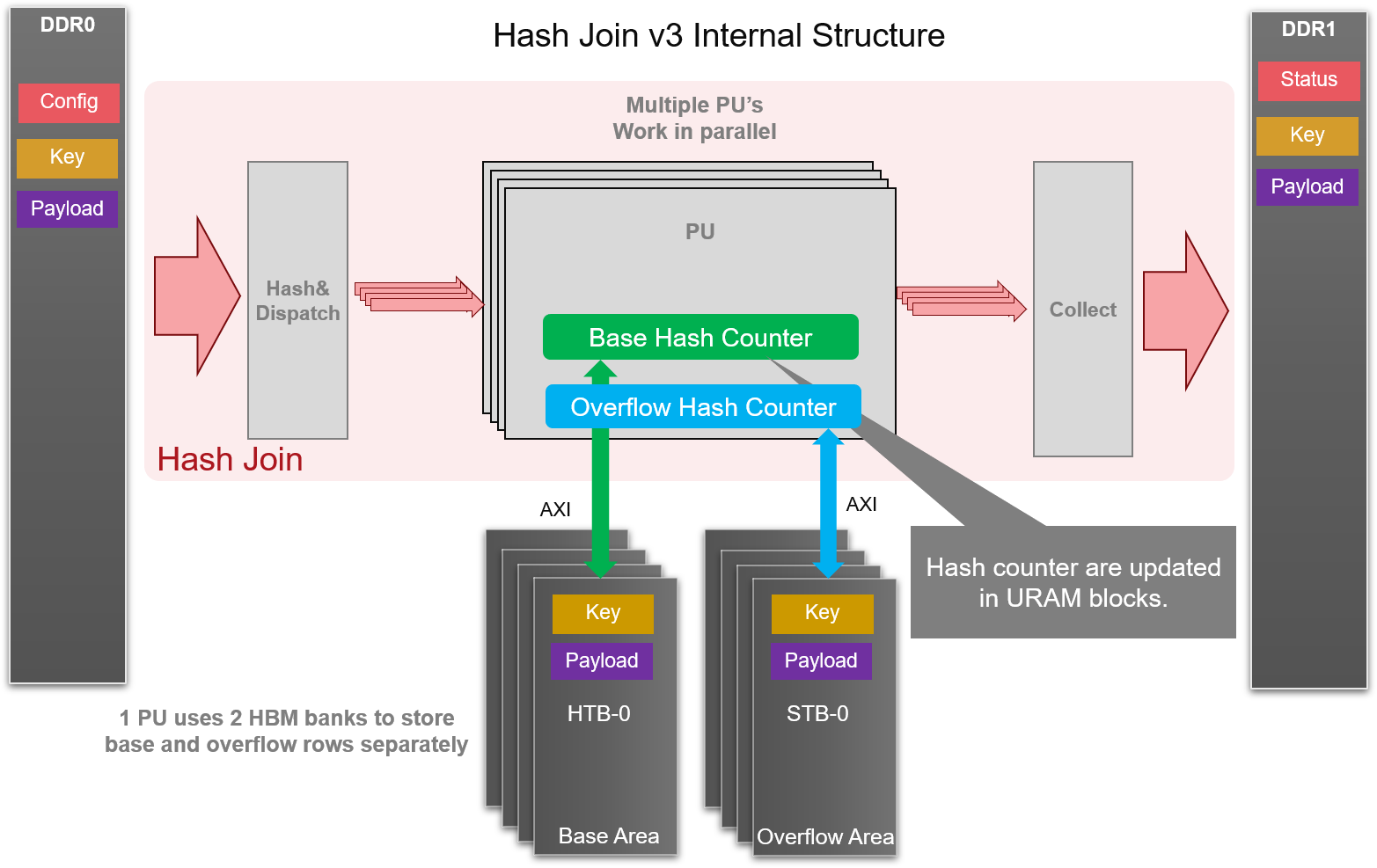
Internals of Hash-Join-v3 and Hash-Build-Probe-v3
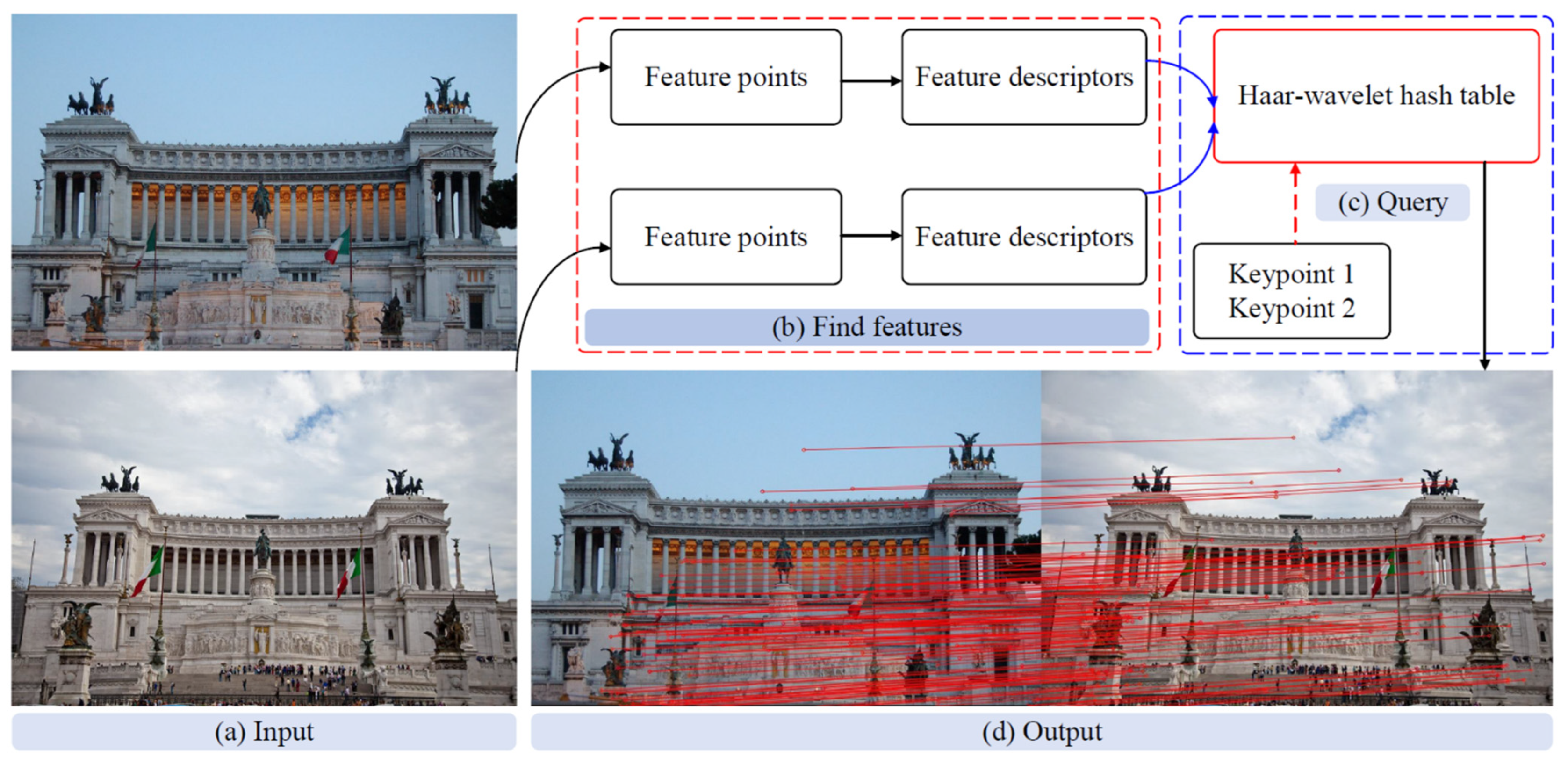
Applied Sciences, Free Full-Text

Similar Image Retrieval Based on Grey-Level Co-Occurrence Matrix

PDF) Extract the Similar Images Using the Grey Level Co

A new design paradigm for provably secure keyless hash function

Comparison of Data Hash generated using Hu moments on KNIX vs






